
Vault was normally signed. |
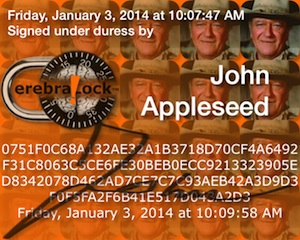
Vault was signed under duress. |

Signature could not be verified because of an error (in this case: the signer's lock is missing). |

|
Copyright ©2014 bitSplit™ Enterprises. All rights reserved. Saturday, March 8, 2014 |
|