|
Each of the vertical strips is a group.
The left (1) has two known items, the right (2) has only one and so is 'less familiar'.
The solution of this screen is therefore 1.
|
| |
 |
The left group has none, the right group has one known item.
This screen represents the digit 2.
|
| |
 |
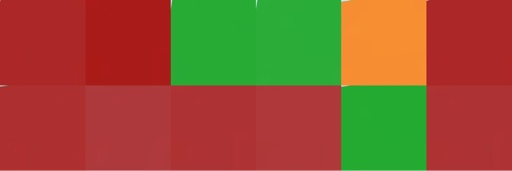
This is the coercion screen.
Each access sequence has one.
The orange item is the coercion item.
Depending on the circumstances, you can treat this as a known item or an unknown item.
So the solution to the screen is 1 or 2.
This screen acts as a fork in the road.
An observer will be unaware which path you choose!
|